The Premium DNS![]() The Domain Name System (DNS) is a hierarchical distributed naming system for computers, services, or any resource connected to the Internet or a private network. It associates various information with domain names assigned to each of the participating entities. A Domain Name Service resolves queries for these names into IP addresses for the purpose of locating computer services and devices worldwide. By providing a worldwide, distributed keyword-based redirection service, the Domain Name System is an essential component of the functionality of the Internet. component of our comprehensive DNS
The Domain Name System (DNS) is a hierarchical distributed naming system for computers, services, or any resource connected to the Internet or a private network. It associates various information with domain names assigned to each of the participating entities. A Domain Name Service resolves queries for these names into IP addresses for the purpose of locating computer services and devices worldwide. By providing a worldwide, distributed keyword-based redirection service, the Domain Name System is an essential component of the functionality of the Internet. component of our comprehensive DNS![]() The Domain Name System (DNS) is a hierarchical distributed naming system for computers, services, or any resource connected to the Internet or a private network. It associates various information with domain names assigned to each of the participating entities. A Domain Name Service resolves queries for these names into IP addresses for the purpose of locating computer services and devices worldwide. By providing a worldwide, distributed keyword-based redirection service, the Domain Name System is an essential component of the functionality of the Internet. service allows you to use the Webnames.ca DNS servers as the authoritative name servers for your domain name. This service gives you control over your DNS records
The Domain Name System (DNS) is a hierarchical distributed naming system for computers, services, or any resource connected to the Internet or a private network. It associates various information with domain names assigned to each of the participating entities. A Domain Name Service resolves queries for these names into IP addresses for the purpose of locating computer services and devices worldwide. By providing a worldwide, distributed keyword-based redirection service, the Domain Name System is an essential component of the functionality of the Internet. service allows you to use the Webnames.ca DNS servers as the authoritative name servers for your domain name. This service gives you control over your DNS records![]() A DNS Record is the basic data element in the domain name system. Each record has a type (A, MX, etc.), an expiration time limit, a class, and some type-specific data. DNS Records provide resolution or translation of domain names to IP address., and other DNS settings through our Premium DNS interface.
A DNS Record is the basic data element in the domain name system. Each record has a type (A, MX, etc.), an expiration time limit, a class, and some type-specific data. DNS Records provide resolution or translation of domain names to IP address., and other DNS settings through our Premium DNS interface.
In addition to the features of our Advanced DNS, Premium DNS also offers the following additional functionality:
- DNS Record Setup during Registration or Transfer
- Set your DNS records prior to purchase or import a zone file.
- DNS Record Versioning
- Each saved instance of a zone file can be instantly recalled and restored at the click of a mouse
- DNS Templates
- Each saved instance of a zone file can be named and used or assigned again later to other domains within your account
- DNS Zone File Import
- Within the creation of DNS Templates is the facility to import a plain text zone file.
- DNS Zone File Export
- Export the current Zone File of a domain to a text file.
- Scheduled DNS Zone File Updates
- Schedule DNS changes to occur at future date and time, complete with email notifications
- Advanced Record Types
- ALIAS Records (ANAME)
- Subdomain
 The Domain Name System (DNS) has a tree structure or hierarchy, with each node on the tree being a domain name. A subdomain is a domain that is part of a larger domain, the only domain that is not also a subdomain is the root domain. For example, mail.example.com and calendar.example.com are subdomains of the example.com domain, which in turn is a subdomain of the com top-level domain (TLD). URL
The Domain Name System (DNS) has a tree structure or hierarchy, with each node on the tree being a domain name. A subdomain is a domain that is part of a larger domain, the only domain that is not also a subdomain is the root domain. For example, mail.example.com and calendar.example.com are subdomains of the example.com domain, which in turn is a subdomain of the com top-level domain (TLD). URL In computing, a uniform resource locator (URL) (originally called universal resource locator) is a specific character string that constitutes a reference to an Internet resource.
Both www.webnames.ca and www.webnames.ca/domain are examples of a URL Redirect
In computing, a uniform resource locator (URL) (originally called universal resource locator) is a specific character string that constitutes a reference to an Internet resource.
Both www.webnames.ca and www.webnames.ca/domain are examples of a URL Redirect - NAPTR Records
- RP Records
- PTR Records
- CAA Records
- TLSA Records
- SOA Record
- Anycast DNS
- Anycast synchronizes a domain's name servers with a distributed cloud of geographically redundant and fault tolerant servers around the world, providing enhanced performance and resilience against DNS-based DDOS attacks.
- DNSSEC
 DNSSEC is designed to protect applications (and caching resolvers serving those applications) from using forged or manipulated DNS data, such as that created by DNS cache poisoning. All answers from DNSSEC protected zones are digitally signed. By checking the digital signature, a DNS resolver is able to check if the information is identical (i.e. unmodified and complete) to the information published by the zone owner and served on an authoritative DNS server.
DNSSEC is designed to protect applications (and caching resolvers serving those applications) from using forged or manipulated DNS data, such as that created by DNS cache poisoning. All answers from DNSSEC protected zones are digitally signed. By checking the digital signature, a DNS resolver is able to check if the information is identical (i.e. unmodified and complete) to the information published by the zone owner and served on an authoritative DNS server.
- DNSSEC is available on all gTLDs and most ccTLDs . This feature allows the verification that your published DNS zone is accurate and has not been altered in transit. When you enable DNSSEC here, we will automatically sign your zone with a cryptographic key and publish the corresponding Delegation Signer (DS) records in the parent registry.
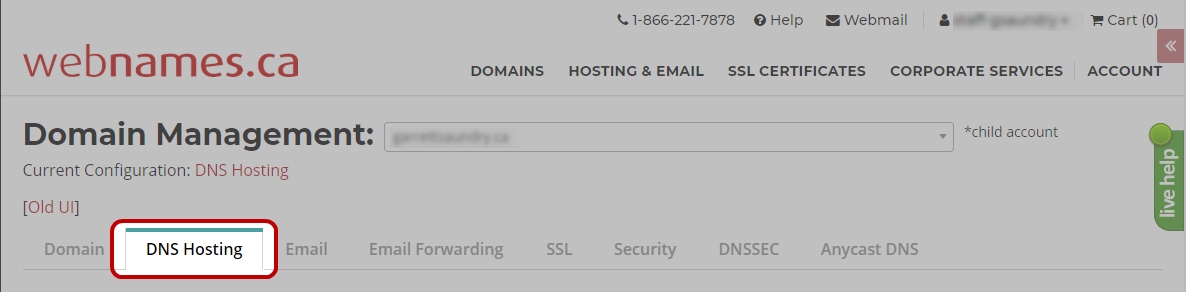
Accessing DNS Hosting Management
To access the DNS Management interface for your domain, navigate the following, starting from the Webnames.ca homepage:
- Click Account
- Click DNS Hosting
- Click on the domain you wish to manage
- Click on the DNS Hosting Tab
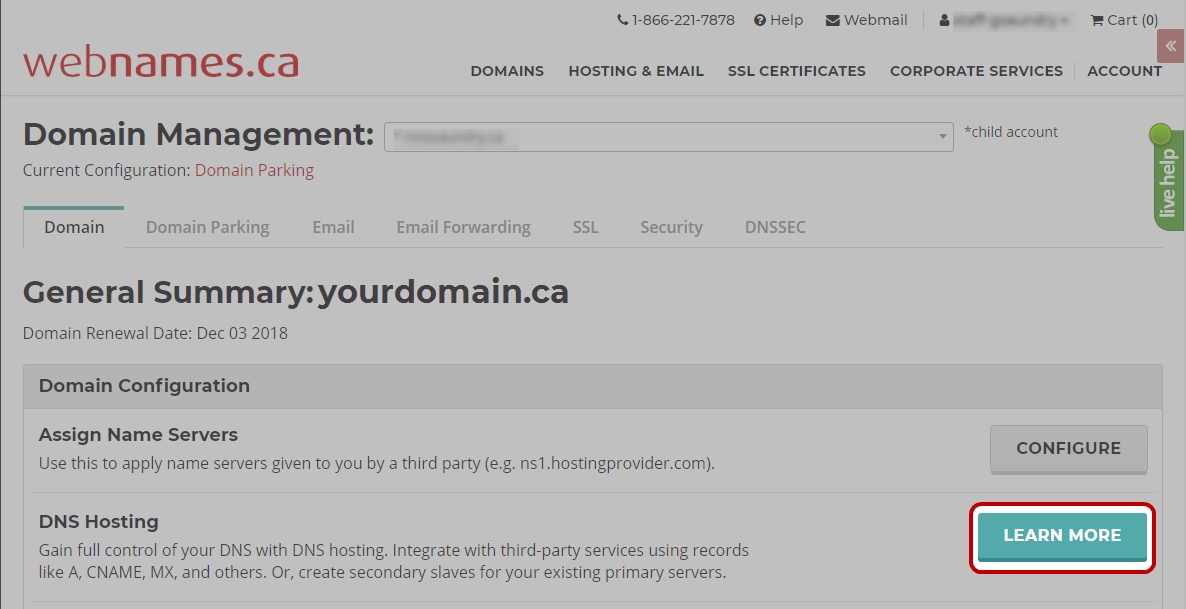
If your domain does not yet have DNS Hosting, click the Learn More button beside DNS Hosting on the Domain Tab.
Interface Overview
The Premium DNS interface is divided into a section on Domain Settings and URL Forwarding, followed by a section for each type of DNS record that can be added and/or managed.
- Host Settings (bothA record
 The A-record is used to translate human friendly domain names such as "www.example.com" into IP-addresses such as 23.211.43.53 (machine friendly numbers). and IPv6
The A-record is used to translate human friendly domain names such as "www.example.com" into IP-addresses such as 23.211.43.53 (machine friendly numbers). and IPv6 IPv6 (Internet Protocol version 6) is the latest revision of the Internet Protocol (IP), the primary communications protocol upon which the entire Internet is built. It is intended to replace the older IPv4, which is still employed for the vast majority of Internet traffic. AAAA record
IPv6 (Internet Protocol version 6) is the latest revision of the Internet Protocol (IP), the primary communications protocol upon which the entire Internet is built. It is intended to replace the older IPv4, which is still employed for the vast majority of Internet traffic. AAAA record An AAAA-record is used to specify the IPv6 address for a host (equivalent of the A-record type for IPv4).
IPv6 is the future replacement for the current IP address system (also known as IPv4).)
An AAAA-record is used to specify the IPv6 address for a host (equivalent of the A-record type for IPv4).
IPv6 is the future replacement for the current IP address system (also known as IPv4).) - Aliases (CNAME record
 CNAME-records are domain name aliases.
To mask this, CNAME-records can be used to give a single computer multiple names (aliases).)
CNAME-records are domain name aliases.
To mask this, CNAME-records can be used to give a single computer multiple names (aliases).) - Mail Exchange (MX record
 MX-records are used to specify the e-mail server(s) responsible for a domain name.
Each MX-record points to the name of an e-mail server and holds a preference number for that server.)
MX-records are used to specify the e-mail server(s) responsible for a domain name.
Each MX-record points to the name of an e-mail server and holds a preference number for that server.) - Delegated Name Servers (NS Record
 NS Resource Records are records in the DNS database to determine which authorative name servers are used for the domain.)
NS Resource Records are records in the DNS database to determine which authorative name servers are used for the domain.) - Text (TXT record
 TXT-records are used to hold descriptive text.
They are often used to hold general information about a domain name such as who is hosting it, contact person, phone numbers, etc.
One common use of TXT-records is for SPF (see http://www.openspf.org).
This is however gradually being replaced by the new SPF-record type.)
TXT-records are used to hold descriptive text.
They are often used to hold general information about a domain name such as who is hosting it, contact person, phone numbers, etc.
One common use of TXT-records is for SPF (see http://www.openspf.org).
This is however gradually being replaced by the new SPF-record type.) - Services (SRV record
 A Service record (SRV record) is a specification of data in the Domain Name System defining the location, i.e. the hostname and port number, of servers for specified services. It is defined in RFC 2782, and its type code is 33. Some Internet protocols such as the Session Initiation Protocol (SIP) and the Extensible Messaging and Presence Protocol (XMPP) often require SRV support by network elements.)
A Service record (SRV record) is a specification of data in the Domain Name System defining the location, i.e. the hostname and port number, of servers for specified services. It is defined in RFC 2782, and its type code is 33. Some Internet protocols such as the Session Initiation Protocol (SIP) and the Extensible Messaging and Presence Protocol (XMPP) often require SRV support by network elements.) - CNAMING of Root Domain (ALIAS Record
 ALIAS pseudo-record type is supported to provide CNAME-like mechanisms on a zone's apex.)
ALIAS pseudo-record type is supported to provide CNAME-like mechanisms on a zone's apex.) - Subdomain URL Redirect
- Naming Authority Pointer (NAPTR record
 A Name Authority Pointer (NAPTR) is a type of resource record in the Domain Name System of the Internet. NAPTR records are most commonly used for applications in Internet telephony, for example, in the mapping of servers and user addresses in the Session Initiation Protocol (SIP).)
A Name Authority Pointer (NAPTR) is a type of resource record in the Domain Name System of the Internet. NAPTR records are most commonly used for applications in Internet telephony, for example, in the mapping of servers and user addresses in the Session Initiation Protocol (SIP).) - Responsible Person (RP record
 Information about the responsible person(s) for the domain. Usually an email address with the @ replaced by a .)
Information about the responsible person(s) for the domain. Usually an email address with the @ replaced by a .) - PTR Records (PTR record
 ) (PTR record
) (PTR record A PTR (Pointer) record is a type of DNS record used for reverse DNS lookups. It maps an IP address to a domain name, essentially the opposite of an A record, which maps a domain name to an IP address.)
A PTR (Pointer) record is a type of DNS record used for reverse DNS lookups. It maps an IP address to a domain name, essentially the opposite of an A record, which maps a domain name to an IP address.) - Certification Authority Authorization (CAA Record
 DNS Certification Authority Authorization (CAA) is an Internet security policy mechanism which uses resource records in the Domain Name System (DNS) to allow domain name holders to specify which certificate authorities are authorized to issue certificates for that domain, and which types of certificates they are able to issue)
DNS Certification Authority Authorization (CAA) is an Internet security policy mechanism which uses resource records in the Domain Name System (DNS) to allow domain name holders to specify which certificate authorities are authorized to issue certificates for that domain, and which types of certificates they are able to issue) - Transport Layer Security Authentication (TLSA Record
 The TLSA record is used to associate a TLS server certificate or public key with the domain name where the record is found, thus forming a "TLSA certificate association".)
The TLSA record is used to associate a TLS server certificate or public key with the domain name where the record is found, thus forming a "TLSA certificate association".) - Authority Setting (SOA record
 Specifies authoritative information about a DNS zone, including the primary name server, the email of the domain administrator, the domain serial number, and several timers relating to refreshing the zone.)
Specifies authoritative information about a DNS zone, including the primary name server, the email of the domain administrator, the domain serial number, and several timers relating to refreshing the zone.)
Zone File Management
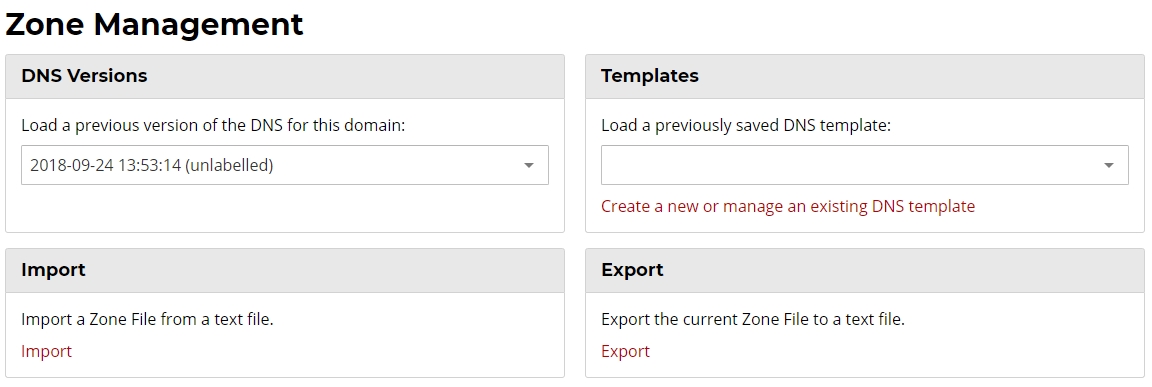
DNS Versions
Each saved instance of your DNS records can be recalled via the drop down. Making a selection from the list will load the DNS records from the version into the interface for review. To apply these records to your domain name, make any changes desired, and then click APPLY at the bottom of the page. A new DNS version will be saved each time the APPLY button is clicked
Templates
Record templates can be created and then later applied to one or more domains within your account.
Click Create a new or manage an existing DNS template to create your initial templates or manage any existing templates.
Import
A text-based version of a zone file (which follows the format outlined in RFC1035(section 5) and RFC1034(section 3.6.1) at https://tools.ietf.org/html/rfc1035 and https://tools.ietf.org/html/rfc1034), can be imported into the Premium DNS interface
- Click Import to go the DNS Templates page
- Click Import Settings from Zone File
- Paste zone file in space provided
- Click Process Zone File
Export
A text-based version of the current zone file can be exported either as a text file or displayed on-screen for simple copying.
- Click Export to go the export interface
- The currently live zone file for the domain is displayed on-screen
- Click Download as Text File to download a copy of the zone file in plain text.
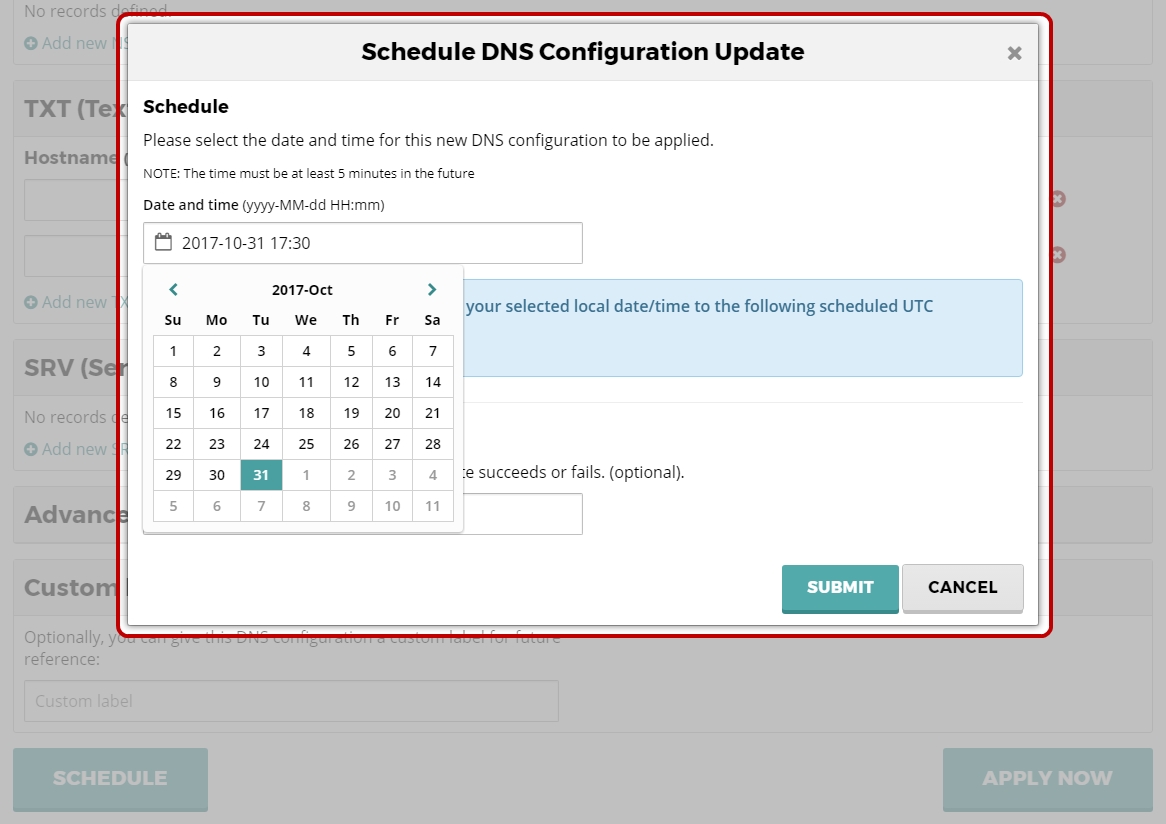
Scheduling DNS Updates
Updates made within the Premium DNS interface can be scheduled to be applied at a future date and time
To schedule an update to be applied in the future:
- Perform the desired DNS updates with the Premium DNS interface
- Click Schedule in the bottom left of the page
- Select a date and time for the update to be applied, using your local time zone. After selection, the selected time will be transposed to UTC and displayed on screen. For clarity, the UTC date and time is what will be used for the application of the zone file update.
- Optionally select one email address to be notified upon success or failure of the update
- Click Submit
Review of Scheduled DNS Updates
Scheduled updates (both upcoming, and past) can be reviewed and managed by browsing to Account -> Manage Scheduled DNS Changes. Note that scheduled DNS updates cannot be edited, however they can be canceled if necessary.
General Configuration
TTL (Time to Live)

The TTL![]() Time to live (TTL) is a mechanism that limits the lifespan of data in a computer or network. Shorter TTLs can cause heavier loads on an authoritative nameserver, but can be useful when changing the address of critical services like Web servers or MX records, and therefore are often lowered by the DNS administrator prior to a service being moved, in order to minimize disruptions. or Time to Live setting controls how long your DNS records will be cached for by other DNS servers. Lowering the TTL
Time to live (TTL) is a mechanism that limits the lifespan of data in a computer or network. Shorter TTLs can cause heavier loads on an authoritative nameserver, but can be useful when changing the address of critical services like Web servers or MX records, and therefore are often lowered by the DNS administrator prior to a service being moved, in order to minimize disruptions. or Time to Live setting controls how long your DNS records will be cached for by other DNS servers. Lowering the TTL![]() Time to live (TTL) is a mechanism that limits the lifespan of data in a computer or network. Shorter TTLs can cause heavier loads on an authoritative nameserver, but can be useful when changing the address of critical services like Web servers or MX records, and therefore are often lowered by the DNS administrator prior to a service being moved, in order to minimize disruptions. value ahead of a planned update to your DNS records will shorten the amount of time it takes for said changes to take effect.
Time to live (TTL) is a mechanism that limits the lifespan of data in a computer or network. Shorter TTLs can cause heavier loads on an authoritative nameserver, but can be useful when changing the address of critical services like Web servers or MX records, and therefore are often lowered by the DNS administrator prior to a service being moved, in order to minimize disruptions. value ahead of a planned update to your DNS records will shorten the amount of time it takes for said changes to take effect.
The TTL setting can be changed by using the dropdown menu indicated in the screenshot above. The default value is 6 hours. The amount of time required for the propagation of an updated TTL value is governed by the TTL value which was initially present on this page.
Example: If your existing TTL value is 6 hours, and you wish to change the value to 15 minutes, Once you update the value to 15 minutes, it will take up to 6 hours for that new value to propagate across the Internet
| NOTE: When selecting 5,15 or 30 minutes as a TTL value, to maintain DNS caching efficiency for your DNS records this value will be reset to 6 hours after 7 days. |
For more information see: http://en.wikipedia.org/wiki/Time_to_live#Time_to_live_of_DNS_records
Root URL Forwarding
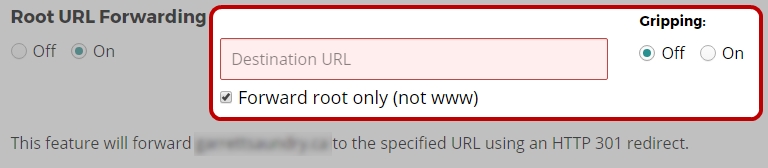
- Select the “On” radio button.
- Type a URL into the “Destination URL” field.
- Select whether or not to apply Gripping to the forward
- A 'Gripped' domain name will maintain the original domain name in the browser address bar, while at the same time displaying the content of the Destination URL. This functionality is dependent on the Destination URL website being compatible with being displayed in an iframe. Not all Destination websites will be compatible with Gripping
- Select whether forward both the root domain and the www to the Destination, or just the root domain (the option to forward both is checked by default, however unchecking this option would be done as part of connecting your domain to a cloud hosting provided. See here for more information)
- Click “Apply Now” at the bottom of the page.
NOTE: To mirror subdirectories of your domain to the domain being forwarded to, include a forward slash at the end of the domain name you specify.
Examples:
| Configured Destination | Client Browses To | Client is Redirected To | Path is forwarded? |
|
http://destination.com |
http://source.com/subpage |
http://destination.com |
No |
|
http://destination.com/ |
http://source.com/subpage |
http://destination.com/subpage |
Yes |
|
http://destination.com/ |
http://source.com/subfolder/subpage.htm |
http://destination.com/subfolder/subpage.htm |
Yes |
|
http://destination.com/ |
http://source.com/subfolder/subpage.htm?param=value#anchor |
http://destination.com/subfolder/subpage.htm |
Yes |
|
http://destination.com/subfolder/ |
http://source.com/subpage |
http://destination.com/subfolder/ |
No |
If the changes were made successfully, you will see the following:

(Note: URL Forwarding will disable any A or CNAME records you have for your domain and www host, as it will point those to the server we use for URL forwarding.)
Gripping
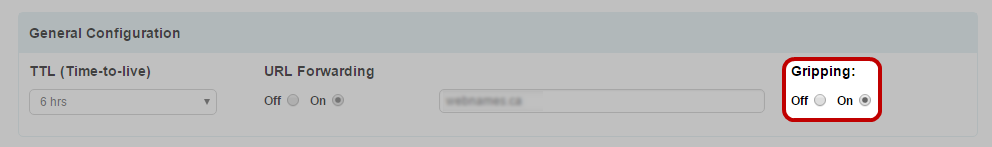
If you want to hide the URL you are forwarding to with your domain name, make sure to turn “Gripping” on before submitting the changes.
DNSSEC
DNSSEC allows the for the verification of your published DNS zone and that it has not been altered in transit. When you enable DNSSEC here, we will automatically sign your zone with a cryptographic key and publish the corresponding Delegation Signer (DS) records in the parent registry. The key will also be rolled over every 180 days automatically. Other than enabling this feature, no other configuration or steps are required to fully implement DNSSEC on your domain. DNSSEC is available on all gTLDs and most ccTLDs
Enabling DNSSEC
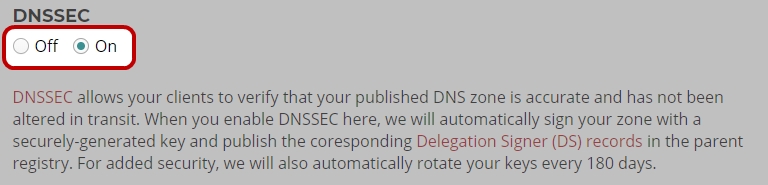
- Under the heading of DNSSEC, toggle the feature to On
- Click “Apply Now” at the bottom of the page.
Host Settings (A Records or AAAA Records)
A records are DNS records which point to an IP address![]() An Internet Protocol address (IP address) is a numerical label assigned to each device (e.g., computer, printer) participating in a computer network that uses the Internet Protocol for communication. An IP address serves two principal functions: host or network interface identification and location addressing. An A record
An Internet Protocol address (IP address) is a numerical label assigned to each device (e.g., computer, printer) participating in a computer network that uses the Internet Protocol for communication. An IP address serves two principal functions: host or network interface identification and location addressing. An A record![]() The A-record is used to translate human friendly domain names such as "www.example.com" into IP-addresses such as 23.211.43.53 (machine friendly numbers). lets you create hostnames and point them to an IP address
The A-record is used to translate human friendly domain names such as "www.example.com" into IP-addresses such as 23.211.43.53 (machine friendly numbers). lets you create hostnames and point them to an IP address![]() An Internet Protocol address (IP address) is a numerical label assigned to each device (e.g., computer, printer) participating in a computer network that uses the Internet Protocol for communication. An IP address serves two principal functions: host or network interface identification and location addressing. As you can see in the example below, we're pointing the hostname www.exampledomain.ca to the IPv4 address 216.251.32.92.
An Internet Protocol address (IP address) is a numerical label assigned to each device (e.g., computer, printer) participating in a computer network that uses the Internet Protocol for communication. An IP address serves two principal functions: host or network interface identification and location addressing. As you can see in the example below, we're pointing the hostname www.exampledomain.ca to the IPv4 address 216.251.32.92.
Adding A Records
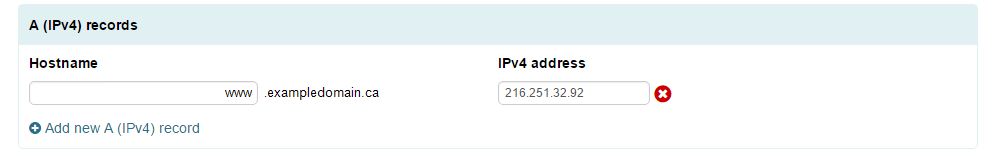
- Click “Add a Record” in the A Records section (or AAAA Records section).
- Enter the host name of your choice in the “Hostname” field, and then enter in the IP address of your server in the IP Address field
- Click “Apply Now” at the bottom of the page.
| Note: The Hostname field should be left blank for at least one entry, this being the entry for your root domain, e.g. exampledomain.ca. The Hostname field should only be populated when assigning records for subdomains, e.g. subdomain.exampledomain.ca An additional "@" symbol is not required, but can be used as a shorthand in the targets of CNAME, MX, NS and SRV records as an alias for the root domain. |
If the changes were made successfully, you will see the following:

Aliases (CNAME Records)
A Canonical Name (CNAME) record causes the specified hostname to become an alias for some other, canonical name. A CNAME record![]() CNAME-records are domain name aliases.
To mask this, CNAME-records can be used to give a single computer multiple names (aliases). useful if you want to associate more than one name with the same collection of A, MX, TXT, etc. records. For example, suppose you have set an A record
CNAME-records are domain name aliases.
To mask this, CNAME-records can be used to give a single computer multiple names (aliases). useful if you want to associate more than one name with the same collection of A, MX, TXT, etc. records. For example, suppose you have set an A record![]() The A-record is used to translate human friendly domain names such as "www.example.com" into IP-addresses such as 23.211.43.53 (machine friendly numbers). and an MX record
The A-record is used to translate human friendly domain names such as "www.example.com" into IP-addresses such as 23.211.43.53 (machine friendly numbers). and an MX record![]() MX-records are used to specify the e-mail server(s) responsible for a domain name.
Each MX-record points to the name of an e-mail server and holds a preference number for that server. for example.com. If you then create a CNAME for mail.example.com and point it to example.com, this will make mail.example.com share the same IP address and MX information as the domain.
MX-records are used to specify the e-mail server(s) responsible for a domain name.
Each MX-record points to the name of an e-mail server and holds a preference number for that server. for example.com. If you then create a CNAME for mail.example.com and point it to example.com, this will make mail.example.com share the same IP address and MX information as the domain.
Note: If you have a CNAME record![]() CNAME-records are domain name aliases.
To mask this, CNAME-records can be used to give a single computer multiple names (aliases). for a particular hostname, you may not have other types of resource records (A, MX, etc.) for that same hostname.
CNAME-records are domain name aliases.
To mask this, CNAME-records can be used to give a single computer multiple names (aliases). for a particular hostname, you may not have other types of resource records (A, MX, etc.) for that same hostname.
Adding a CNAME Record
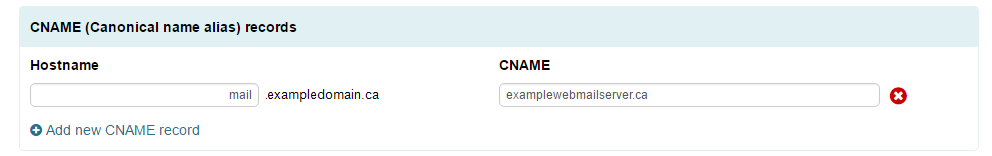
- Click “Add a Record” in the CNAME Records section.
- Enter the host name of your choice in the “Hostname” field, and then enter in the hostname of your server you want to alias to.
- Click “Apply Now” at the bottom of the page.
If the changes were made successfully, you will see the following:

Mail Exchange (MX Records)
MX or Mail Exchanger Records as they are also known are used to specify how the SMTP![]() Simple Mail Transport Protocol: An Internet standard for electronic mail (e-mail) transmission across Internet Protocol (IP) networks.This is the protocol used to send email. (Simple Mail Transfer Protocol) routes email messages. If you have email services on your domain name either with Webnames.ca or a third party, it is imperative that you create MX records correctly, or your emails will not work.
Simple Mail Transport Protocol: An Internet standard for electronic mail (e-mail) transmission across Internet Protocol (IP) networks.This is the protocol used to send email. (Simple Mail Transfer Protocol) routes email messages. If you have email services on your domain name either with Webnames.ca or a third party, it is imperative that you create MX records correctly, or your emails will not work.
An MX record cannot be pointed to an IP address directly; they must be pointed to a hostname. Usually one would create an A record pointing to the mail server IP address, and then create an MX record pointing to the hostname.
The MX hostname should typically be your domain name, as it will determine what your email addresses are. If your MX hostname is “example.com ”, then your email addresses will be “user@example.com ”. This is done by simply leaving the Hostname field blank.
However, if you use mail.example.com as your MX hostname, then your email addresses will be “user@mail.example.com ”, which is generally not a good thing.
For redundancy, you can use more than one MX record to point to multiple mail servers. Which mail server is used first is determined by the priority value. The lower the priority value, the higher the actual priority will be.
Adding an MX Record
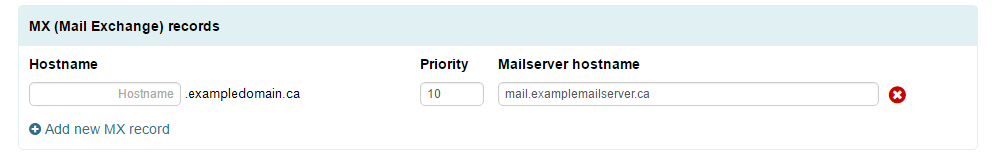
- Click “Add a Record” in the MX Records section.
- Leave the hostname field blank.
- Enter a priority value (Lower numbers means a higher priority.)
- Enter the hostname of the mail server in the “Mail Server Name” field
- Click “Apply Now” at the bottom of the page.
If the changes were made successfully, you will see the following:

Delegate Subdomains (NS Records)
In order to have Subdomains of your domain serviced by alternate name servers (i.e. other than ns1.webnames.ca etc.), delegation can be used by way of an NS record![]() NS Resource Records are records in the DNS database to determine which authorative name servers are used for the domain. for the subdomain in question.
NS Resource Records are records in the DNS database to determine which authorative name servers are used for the domain. for the subdomain in question.
- Click “Add a Record” in the NS Records section.
- Enter the host name (subdomain) of your choice in the “Hostname” field, and then enter in the name server
 In computing, a name server is a computer server that hosts a network service for providing responses to queries against a directory service. It maps a human-recognizable identifier to a system-internal, often numeric, identification or addressing component. This service is performed by the server according to a network service protocol. name you wish to delegate to.
In computing, a name server is a computer server that hosts a network service for providing responses to queries against a directory service. It maps a human-recognizable identifier to a system-internal, often numeric, identification or addressing component. This service is performed by the server according to a network service protocol. name you wish to delegate to. - Click “Apply Now” at the bottom of the page.
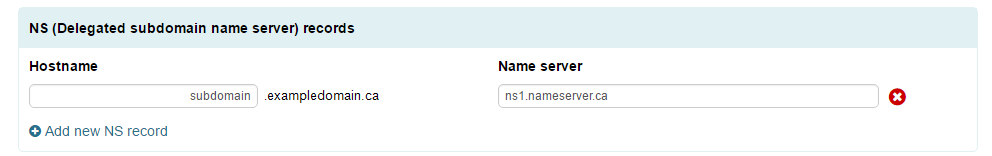
If the changes were made successfully, you will see the following:

TXT Records
TXT are simply plain text records. They allow you to associate text to a host name. Currently a primary use for TXT records is for the implementation of SPF![]() Sender Policy Framework (SPF) is an email authentication method which ensures the sending mail server is authorized to originate mail from the email sender's domain. records. For information on SPF, please see: http://en.wikipedia.org/wiki/Sender_Policy_Framework
Sender Policy Framework (SPF) is an email authentication method which ensures the sending mail server is authorized to originate mail from the email sender's domain. records. For information on SPF, please see: http://en.wikipedia.org/wiki/Sender_Policy_Framework
Adding a TXT Record
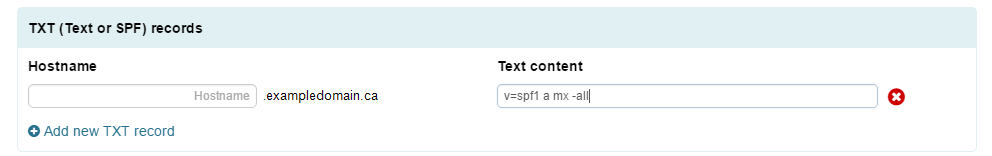
- Click “Add new TXT Record” in the TXT Records section.
- Enter in the hostname of your choice in the Hostname field.
- Type in your text string into the TXT field.
- Click “Apply Now” at the bottom of the page.
If the changes were made successfully, you will see the following:

Services (SRV Records)
SRV records are required by services such as the SIP or XMPP Instant Messaging protocols. Microsoft Exchange servers also make use of SRV records. As you'll notice SRV records have more parameters than other records. The parameters are as follows:
Priority: Priority of the target host, lower the value, the higher the priority.
Weight: If more then one SRV record![]() A Service record (SRV record) is a specification of data in the Domain Name System defining the location, i.e. the hostname and port number, of servers for specified services. It is defined in RFC 2782, and its type code is 33. Some Internet protocols such as the Session Initiation Protocol (SIP) and the Extensible Messaging and Presence Protocol (XMPP) often require SRV support by network elements. share the same priority, then the DNS server will consider the weight.
A Service record (SRV record) is a specification of data in the Domain Name System defining the location, i.e. the hostname and port number, of servers for specified services. It is defined in RFC 2782, and its type code is 33. Some Internet protocols such as the Session Initiation Protocol (SIP) and the Extensible Messaging and Presence Protocol (XMPP) often require SRV support by network elements. share the same priority, then the DNS server will consider the weight.
Port: The TCP or UDP port used by the service.
Target: The canonical hostname of the machine providing the service.
Adding an SRV Record
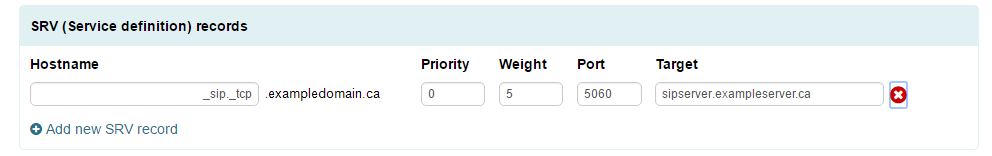
- Click “Add new SRV Record” in the SRV Records section.
- In the hostname field, you must specify the service name preceded by an underscore (in this case it's sip) then a dot, followed by another underscore and he protocol. (In this case it's TCP.)
- Enter in a priority and weight.
- Specify the port the server is listening on.
- Specify the target, which is the hostname assigned to the server hosting the service.
- Click “Apply Now” at the bottom of the page.
If the changes were made successfully, you will see the following:

Advanced Record Types
ALIAS Records
ALIAS pseudo-record type is supported to provide CNAME-like mechanisms on a zone's apex. While not a true DNS record type, the ability to forward the root of a domain name to another domain name has become an increasingly in-demand feature, especially when associating a domain name with website hosted on cloud-based providers.
The use of the Alias record at the apex (root) of a domain name will not have adverse effect on subdomains nor email, such as when a CNAME record is utilized.
Adding an Alias Record
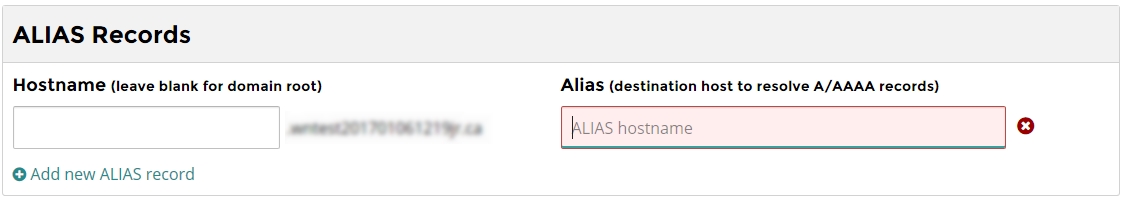
- Populate the Hostname field if the forwarding is to be applied only to a specific subdomain (e.g. subdomain.yourdomain.ca) To forward the root of the domain (e.g. yourdomain.ca), leave the hostname field blank.
- Populate the Alias field with the address the domain should be forwarded to (e.g. myhostingprovider.com)
- Click “Apply Now” at the bottom of the page.
If the changes were made successfully, you will see the following:

Subdomain URL Redirect
While not a specific record type, this section of the DNS record editor allows for the forwarding of multiple subdomains to other discrete URLs, similar to our See also: Premium DNS.
Adding a Subdomain URL Redirect
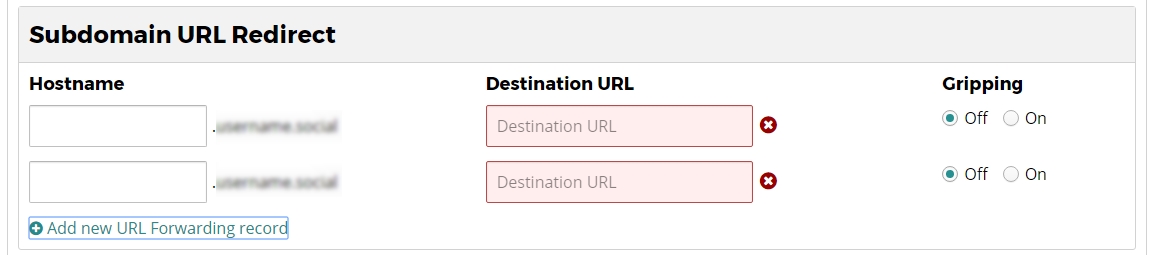
- Type a URL into the “Forwarding To:” field.
- Select whether or not to apply Gripping to the forward
- A 'Gripped' domain name will maintain the original domain name in the browser address bar, while at the same time displaying the content of the Destination URL. This functionality is dependent on the Destination URL website being compatible with being displayed in an iframe. Not all Destination websites will be compatible with Gripping
- Click “Apply Now” at the bottom of the page.
NOTE: To mirror subdirectories of your domain to the domain being forwarded to, include a forward slash at the end of the domain name you specify.
Examples:
| Configured Destination | Client Browses To | Client is Redirected To | Path is forwarded? |
|
http://subdomain.destination.com |
http://source.com/subpage |
http://subdomain.destination.com |
No |
|
http://subdomain.destination.com |
http://source.com/subpage |
http://subdomain.destination.com/subpage |
Yes |
|
http://subdomain.destination.com |
http://source.com/subfolder/subpage.htm |
http://subdomain.destination.com/subfolder/subpage.htm |
Yes |
|
http://subdomain.destination.com |
http://source.com/subfolder/subpage.htm?param=value#anchor |
http://subdomain.destination.com/subfolder/subpage.htm |
Yes |
|
http://subdomain.destination.com/subfolder/ |
http://source.com/subpage |
http://subdomain.destination.com/subfolder/ |
No |
If the changes were made successfully, you will see the following:

NAPTR Records
Naming Authority Pointer Records were originally produced as a way to encode rule-sets in DNS so that a regular expression would be used by a client program to rewrite a string into a domain name.
The function of rewriting a string according to rules in a record has usefulness in several different applications. The reasons the rewrite is used, what the expected outcomes are, or what they are used for, are all specified by applications that will ultimately utilize them.
Flags and other fields are also specified in the NAPTR to control the rewrite procedure in various ways or to provide information on how to communicate with the host at the domain name that was the result of the rewrite.
Adding a NAPTR Record
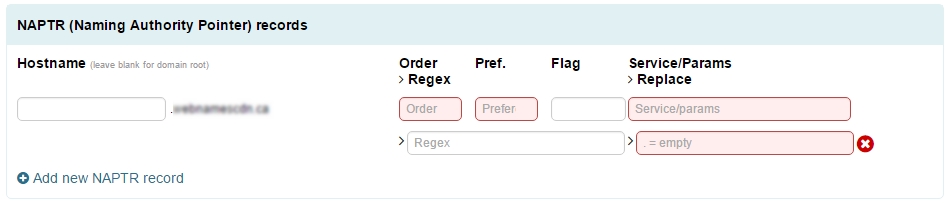
- Click “Add new NAPTR Record” in the RP Records section.
- Enter in the hostname of your choice in the Hostname field.
- Type in the desired values for the following fields
- Order*
- Preference*
- Flag
- Service / Parameters*
- Regex
- Replace*
- * Denotes required values
- Click “Apply Now” at the bottom of the page.
If the changes were made successfully, you will see the following:

RP Records
The Responsible Person Record defines information about the responsible person(s) for the domain.
Adding an RP Record
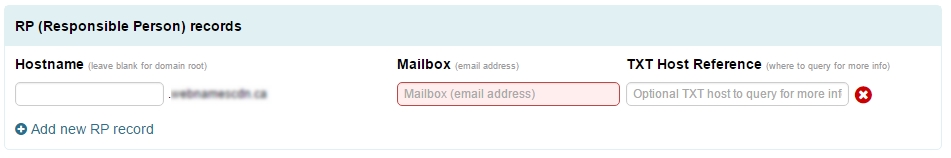
- Click “Add new RP Record” in the RP Records section.
- Enter in the hostname of your choice in the Hostname field.
- Type in the desired email address into the Mailbox field.
- Optionally, provide an additional Host Reference value
- Click “Apply Now” at the bottom of the page.
If the changes were made successfully, you will see the following:

|
NOTE: The email address should be entered into the field verbatim. Note that RP records often utilize a . in place of the @ symbol. For simplicity, our system will accept the verbatim email address (though one in which the @ has already been replaced with a . will also be accepted)and then perform any necessary character replacements before committing the value to DNS. If the email address being utilized contains a dot within the local portion of the address (i.e. to the left of the @), then those additional dots can be escaped by using a backslash. e.g. host.master@example.ca would be host\.master@example.ca. The above is not required for additional dots appearing within the domain name, such as hostmaster@example.bc.ca . This address can be entered in verbatim. |
PTR Records
Pointer to a canonical name. Pointer Records are used to perform IP address resolution (as opposed to name resolution), and as such, function conversely to A records. They are there fore used most commonly to implement reverse DNS lookups.
In following the reverse DNS function, PTR records are assigned to an IP address and are used to resolve the IP address to a name. Therefore. PTR records are normally created and hosted by the IP address provider (ISP etc).
Pointer Records can however be delegated by one IP provider to another provider, and in this context Webnames can host PTR Records.
Adding a PTR Record
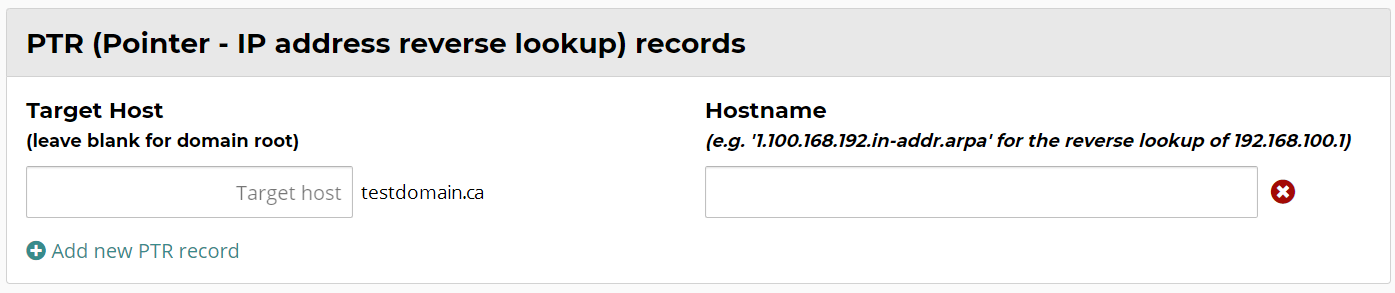
- Click Add new PTR Record
 PTR-records are primarily used as "reverse records" - to map IP addresses to domain names (reverse of A-records and AAAA-records).
PTR-records are primarily used as "reverse records" - to map IP addresses to domain names (reverse of A-records and AAAA-records). - Enter in the hostname of your choice in the Hostname field (or leave blank to apply the record to the root of the domain).
- Enter the reverse DNS value as provided by your IP Address provider.
- Click “Apply Now” at the bottom of the page.
CAA Records
DNS Certification Authority Authorization (CAA)![]() DNS Certification Authority Authorization (CAA) is an Internet security policy mechanism which uses resource records in the Domain Name System (DNS) to allow domain name holders to specify which certificate authorities are authorized to issue certificates for that domain, and which types of certificates they are able to issue is an Internet security policy mechanism which uses resource records in the Domain Name
DNS Certification Authority Authorization (CAA) is an Internet security policy mechanism which uses resource records in the Domain Name System (DNS) to allow domain name holders to specify which certificate authorities are authorized to issue certificates for that domain, and which types of certificates they are able to issue is an Internet security policy mechanism which uses resource records in the Domain Name![]() A domain name is an identification string that defines a realm of administrative autonomy, authority, or control on the Internet. Domain names are formed by the rules and procedures of the Domain Name System (DNS). System (DNS) to allow domain name holders to specify which certificate authorities are authorized to issue certificates for that domain, and which types of certificates they are able to issue.
A domain name is an identification string that defines a realm of administrative autonomy, authority, or control on the Internet. Domain names are formed by the rules and procedures of the Domain Name System (DNS). System (DNS) to allow domain name holders to specify which certificate authorities are authorized to issue certificates for that domain, and which types of certificates they are able to issue.
Adding a CAA Record
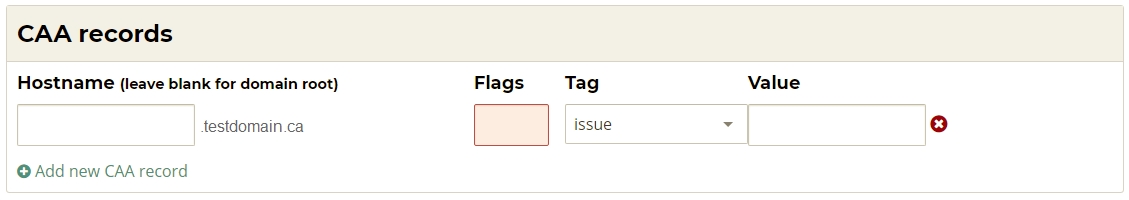
- Click “Add new CAA Record
 DNS Certification Authority Authorization (CAA) is an Internet security policy mechanism which uses resource records in the Domain Name System (DNS) to allow domain name holders to specify which certificate authorities are authorized to issue certificates for that domain, and which types of certificates they are able to issue” in the RP Records section.
DNS Certification Authority Authorization (CAA) is an Internet security policy mechanism which uses resource records in the Domain Name System (DNS) to allow domain name holders to specify which certificate authorities are authorized to issue certificates for that domain, and which types of certificates they are able to issue” in the RP Records section. - Enter in the hostname of your choice in the Hostname field (or leave blank to apply the record to the root of the domain).
- Enter the desired Flag value:
- A Flag value of 128 or more is an indication to a CA which does not understand or does not implement the Tag value specified in the record to refuse to issue a certificate for domain identified in the hostname field in step 2, above.
- A Flag value of 127 or less will result in no action or further consideration by a CA.
- Select the desired Tag value:
- ISSUE This property authorizes the holder of the domain specified in the "value" field to issue certificates for the domain for which the property is published.
- ISSUEWILD This property acts like issue but allows wildcard certificates.
- IODEF This property specifies a method for CAs to report to the domain holder when a certificate is issued. Not all CAs support this tag, so there is no guarantee that all certificate issuances will be reported.
- Define the Value for the Record
- For ISSUE and ISSUEWILD tags, the value specifies the CA which is to be permitted to issue certificates for the domain identified in the hostname field in step 2, above. To prohibit the issuance of certificates, a value of ';' is used.
- For IODEF tags, provide an email address which will be notified upon issuance of an SSL
 Transport Layer Security (TLS) and its predecessor, Secure Sockets Layer (SSL), are cryptographic protocols that provide communication security over the Internet.[1] TLS and SSL encrypt the segments of network connections at the Application Layer for the Transport Layer, using asymmetric cryptography for key exchange, symmetric encryption for confidentiality, and message authentication codes for message integrity. certificate for the domain identified in the hostname field in step 2, above. Alternatively, a URL can be supplied as a destination for RID Message, if supported by the CA.
Transport Layer Security (TLS) and its predecessor, Secure Sockets Layer (SSL), are cryptographic protocols that provide communication security over the Internet.[1] TLS and SSL encrypt the segments of network connections at the Application Layer for the Transport Layer, using asymmetric cryptography for key exchange, symmetric encryption for confidentiality, and message authentication codes for message integrity. certificate for the domain identified in the hostname field in step 2, above. Alternatively, a URL can be supplied as a destination for RID Message, if supported by the CA.
- Click “Apply Now” at the bottom of the page.
| NOTE: More than one CAA Record for a particular hostname may be created. For example, one ISSUE and one IODEF record may be created. |
Transport Layer Security Authentication (TLSA Record)
A Transport Layer Security Authentication (TLSA) Record![]() The TLSA record is used to associate a TLS server certificate or public key with the domain name where the record is found, thus forming a "TLSA certificate association". is used to allow X.509 certificates, commonly used for Transport Layer Security (TLS
The TLSA record is used to associate a TLS server certificate or public key with the domain name where the record is found, thus forming a "TLSA certificate association". is used to allow X.509 certificates, commonly used for Transport Layer Security (TLS![]() The Transport Layer Security protocol aims primarily to provide privacy and data integrity between two communicating computer applications.[1]:3 When secured by TLS, connections between a client (e.g., a web browser or email program) and a server (website or email server) are private (or secure), authenticated, and unaltered.), to be bound to DNS names using Domain Name System Security Extensions (DNSSEC) as a way to authenticate TLS client and server entities without a certificate authority (CA).
The Transport Layer Security protocol aims primarily to provide privacy and data integrity between two communicating computer applications.[1]:3 When secured by TLS, connections between a client (e.g., a web browser or email program) and a server (website or email server) are private (or secure), authenticated, and unaltered.), to be bound to DNS names using Domain Name System Security Extensions (DNSSEC) as a way to authenticate TLS client and server entities without a certificate authority (CA).
Adding a TLSA Record
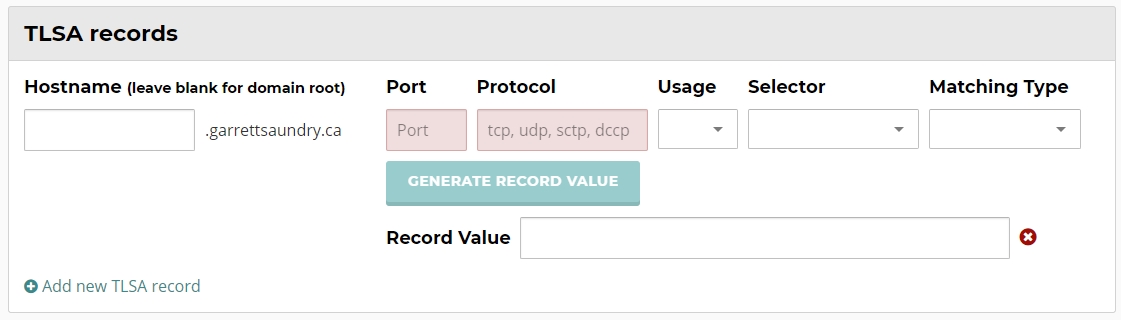
- Click Add new TLSA Record
- Enter in the hostname of your choice in the Hostname field (or leave blank to apply the record to the root of the domain).
- Enter the desired Port number (typically 443)
- Enter the desired Protocol (typically tcp)
- Select the desired Usage value
- 0 PKIK-TA: Certificate Authority Constraint
- 1 PKIX-EE: Service Certificate Constraint
- 2 DANE-TA: Trust Anchor Assertion
- 3 DANE-EE: Domain Issue Certificate
- Choose a Selector Value
- 0 Cert: Use Full Certificate
- 1 SPKI: Use Subject Public Key
 The key that a user allows the world to know in asymmetric encryption. It can encrypt or decrypt data for a single transaction but cannot do both.
The key that a user allows the world to know in asymmetric encryption. It can encrypt or decrypt data for a single transaction but cannot do both.
- Select the desired Matching Type value
- 0 Full: No Hash
- 1 SHA-256: SHA-256 Hash
- 2 SHA-512: SHA-512 Hash
- Enter or Generate a Record Value
- If choosing to generate a Record Value, in the subsequent pop-up window paste in the entirety of the Certificate which the TLSA record will pertain to. A Record Value will then be generated using a combination of the previously chosen Selector Value, Matching Type and the Certificate itself.
- Click “Apply Now” at the bottom of the page.
Authority Setting (SOA Record)
The Start of Authority or SOA record![]() Specifies authoritative information about a DNS zone, including the primary name server, the email of the domain administrator, the domain serial number, and several timers relating to refreshing the zone. determines how often the secondary servers will refresh their information with the primary name server, as well as how long to wait before retrying if the connection fails. It also controls how long to wait before giving up if the connection keeps failing.
Specifies authoritative information about a DNS zone, including the primary name server, the email of the domain administrator, the domain serial number, and several timers relating to refreshing the zone. determines how often the secondary servers will refresh their information with the primary name server, as well as how long to wait before retrying if the connection fails. It also controls how long to wait before giving up if the connection keeps failing.
This particular section should not need to be edited, except by advanced users. The default settings for this section are all fairly standard, and changing them would not have a large impact on your DNS.
Custom Label
The DNS records on page can be given a label and saved for future re-use or reference within the Version portion of the interface
Schedule
In addition to applying DNS updates instantly, updates can instead be schedule to be applied at a future date and time. See also: Premium DNS